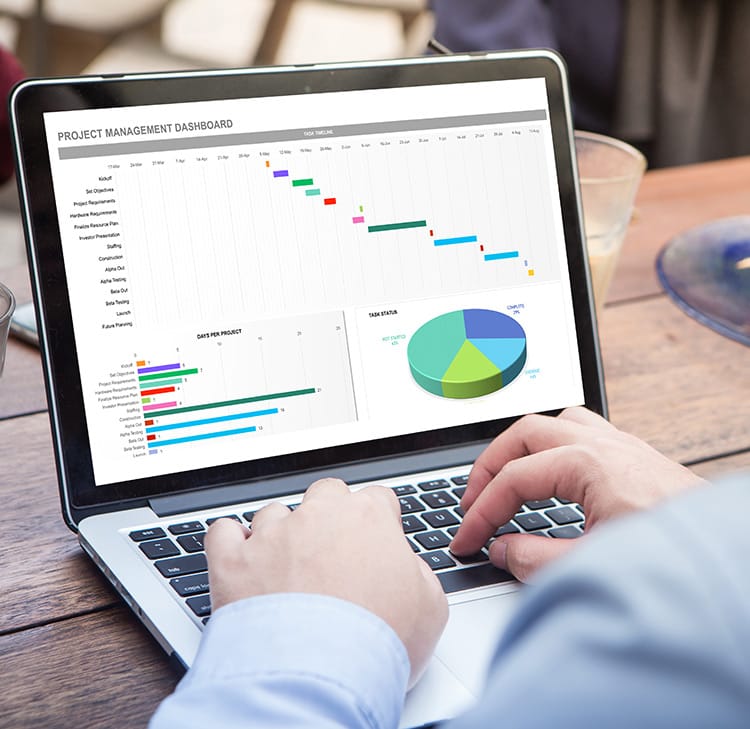
IT & Cyber Security Training Courses
Ensuring a Secure Digital Future through Efficient Cyber Security





Cyber Security, Information Governance, Legal Risk Management and Compliance with ISO Records Management Controls



Cyber Security, Information Governance, Legal Risk Management and Compliance with ISO Records Management Controls
About Our IT & Cyber Security Training Courses
IT and Cyber Security Training Courses at Euromatech are designed to equip professionals with the essential skills, frameworks, and technical knowledge needed to safeguard digital systems, protect organizational data, and ensure business continuity in a rapidly evolving cyber landscape. As digital transformation accelerates, the importance of defending networks, applications, and critical infrastructure has never been greater. Our courses combine technical expertise with strategic insight, ensuring participants can build resilient cyber defenses and lead secure digital operations.
These Cyber Security Courses explore both foundational and advanced topics across the IT and cybersecurity spectrum. Participants learn how to detect and respond to threats, manage cyber risks, implement data protection policies, and align technology strategies with business objectives. Courses also address the growing need for leadership in digital transformation — helping professionals understand not only how to manage security, but also how to integrate it seamlessly into innovation and operational excellence.
The training extends beyond technical skill-building to include governance, compliance, and risk management. Participants gain practical insights into developing cybersecurity frameworks, managing security operations, and responding to incidents in real time. Specialized sessions focus on key areas such as cyber resilience, asset integrity, and process safety — highlighting how modern industries must integrate safety and cybersecurity principles to mitigate risk effectively.
By blending real-world case studies with global best practices, Euromatech’s IT & Cyber Security Training Courses prepare professionals to handle complex challenges in areas such as cloud computing, digital assets, industrial systems, and enterprise IT environments. Whether participants are technical specialists, risk managers, or decision-makers, they leave equipped to make informed decisions that strengthen their organization’s cyber posture, ensure regulatory compliance, and protect business value in a connected world.
Key Benefits of IT & Cyber Security Training Courses
Our IT and Cyber Security Courses are designed to provide practical, strategic, and technical knowledge that supports modern organizational resilience.
- Gaining in-depth knowledge of cybersecurity fundamentals and emerging threats
- Learning to identify vulnerabilities and design comprehensive defense strategies
- Strengthening digital risk management and incident response capabilities
- Understanding the link between asset integrity, safety, and cybersecurity
- Building leadership skills for managing secure digital transformation initiatives
- Enhancing awareness of compliance and governance frameworks for data protection
- Applying global cybersecurity best practices across diverse business environments
Target Audience
These IT & Cyber Security Training Courses are suited for professionals seeking to enhance their technical expertise and leadership in digital security management.
- IT professionals, system administrators, and cybersecurity analysts
- Chief Technology Officers and digital transformation leaders
- Security managers and risk officers responsible for cyber resilience
- Engineers managing industrial assets and process safety systems
- Compliance and audit professionals ensuring cybersecurity standards are met
- Consultants advising clients on IT and cybersecurity strategy
- Executives and decision-makers overseeing information and technology assets
FAQ
We are happy to share the profiles of our expert instructors. To learn more about their qualifications and experience, please contact us [email protected]
Yes, we provide tailored training solutions designed to meet the specific needs of your organization. Customized courses can be delivered either in-person or online, and you can select the dates and duration that best fit your schedule. For more details, please contact us at [email protected]
Yes, we can assist you with the following:
- Corporate Discount: If available, we can extend our corporate discount for your stay at selected hotels.
- Hotel Suggestions: We can provide recommendations for nearby hotels based on your preferences and budget.
Feel free to explore online booking platforms for the most cost-effective options.
These courses explore a full range of subjects, including cybersecurity frameworks, network defense, data protection, and incident response. Participants also gain knowledge in governance, risk, and compliance, as well as asset integrity management, which connects operational safety with digital resilience. The content balances both technical and strategic dimensions to prepare professionals for diverse cybersecurity challenges.
Yes. While some courses focus on technical competencies, others are tailored for managers, executives, and decision-makers who oversee technology, compliance, or risk functions. Non-technical participants learn how to interpret cybersecurity reports, manage digital risks, and make informed strategic decisions that protect business operations.
They provide the frameworks, tools, and methodologies required to anticipate, prevent, and respond to cyber threats. Participants learn how to design layered defenses, implement proactive monitoring systems, and establish clear response procedures. This ensures organizations are prepared to handle disruptions effectively while maintaining business continuity and trust
Governance and compliance are at the core of all cybersecurity efforts. The courses emphasize how to align IT practices with international standards and regulations such as ISO 27001, GDPR, and NIST frameworks. Participants learn how to integrate these standards into operational policies, ensuring that their organizations remain compliant while safeguarding critical data and infrastructure.
Yes. The training emphasizes real-world applications through case studies, practical exercises, and interactive discussions. Participants leave with actionable tools for assessing vulnerabilities, implementing control systems, and improving digital security measures. The knowledge gained enables them to strengthen existing frameworks and proactively address emerging cyber risks.